收到伺服器401響應的處理(HTTP或SIP)
Digest access authentication
HTTP Digest access authentication is one of the agreed methods a web server can use to negotiate credentials with a web user (using the HTTP protocol). Digest authentication is intended to supersede unencrypted use of the Basic access authentication, allowing user identity to be established securely without having to send a
[edit]Overview
Digest access authentication was originally specified by RFC 2069 (An Extension to HTTP: Digest Access Authentication
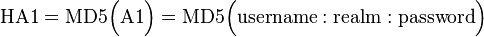
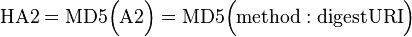

RFC 2069 was later replaced by RFC 2617 (HTTP Authentication: Basic and Digest Access Authentication). RFC 2617 introduced a number of optional security enhancements to Digest Authentication; "Quality of Protection" (qop), nonce counter incremented by client, and a client generated random nonce. These enhancements are designed to protect against e.g.
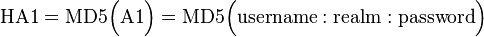
If the qop directive's value is "auth" or is unspecified, then HA2 is
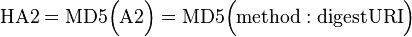
If the qop directive's value is "auth-int" , then HA2 is

If the qop directive's value is "auth" or "auth-int" , then compute the response as follows:
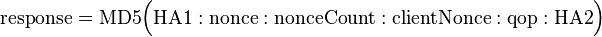
If the qop directive is unspecified, then compute the response as follows:

(The above shows that when qop is not specified, the simpler RFC 2069 standard is followed).
[edit]Impact of MD5 security on Digest authentication
The MD5 calculations used in HTTP Digest Authentication is intended to be "one way", meaning that it should be difficult to determine the original input when only the output is known. If the password itself is too simple, however, then it may be possible to test all possible inputs and find a matching output (a brute force attack) – perhaps aided by a dictionary or suitable look-up list. For the most security, users should use long, non-trivial passwords - however this is not ideal since it is an inconvenience on the user-side.
The HTTP scheme was designed at CERN in 1993 and does not incorporate subsequent improvements in authentication systems, such as the development of keyed-hash message authentication code (HMAC). Although the cryptographic construction that is used is based on the MD5hash function, collision attacks were in 2004 generally believed (e.g. Hash collision news) to not affect applications where the plaintext (i.e. password) is not known. However, claims in 2006 (Kim, Biryukov2, Preneel, Hong On the Security of HMAC and NMAC Based on HAVAL MD4 MD5 SHA-0 and SHA-1) cause some doubt over other MD5 applications as well. However, so far MD5 collision attacks have not been shown to pose a threat to Digest Authentication, and the RFC 2617 allows servers to implement mechanisms to detect some collision and replay attacks.
[edit]HTTP Digest Authentication considerations
[edit]Advantages
HTTP Digest authentication is designed to be more secure than traditional digest authentication schemes; "significantly stronger than (e.g.)CRAM-MD5 ..." (RFC2617).
Some of the security strengths of HTTP Digest authentication are:
- The password is not used directly in the digest, but rather HA1 = MD5(username:realm:password). This allows some implementations (e.g.JBoss DIGESTAuth) to store HA1 rather than the clear text password.
- Client nonce was introduced in RFC2617, which allows the client to prevent chosen plaintext attacks (which otherwise makes e.g. rainbow tables a threat to digest authentication schemes).
- Server nonce is allowed to contain timestamps. Therefore the server may inspect nonce attributes submitted by clients, to prevent replay attacks.
- Server is also allowed to maintain a list of recently issued or used server nonce values to prevent reuse.
[edit]Disadvantages
Digest access authentication is intended as a security trade-off; it is intended to replace unencrypted HTTP Basic access authentication which is extremely weak. However it is not intended to replace strong authentication protocols, such as Public key or Kerberos authentication.
In terms of security, there are several drawbacks with Digest access authentication:
- Many of the security options in RFC2617 are optional. If quality-of-protection (qop) is not specified by the server, the client will operate in a security-reduced legacy RFC2069 mode.
- Digest access authentication is vulnerable to Man-in-the-middle attack; for example, a MitM attacker could tell clients to use Basic access authentication or legacy RFC2069 Digest access authentication mode. To extend this further, Digest access authentication provides no mechanism for clients to verify the server's identity.
- Some servers require passwords to be stored using reversible encryption. However, it is possible to instead store the digested value of the username, realm, and password.[1]
[edit]Alternative authentication protocols
Some strong authentication protocols for web based applications include:
- Public key authentication (usually implemented with HTTPS / SSL client certificates).
Weak cleartext protocols are also often in use:
These weak cleartext protocols used together with HTTPS network encryption resolve many of the threats that Digest access authentication is designed to prevent.
[edit]Example with explanation
Warning: Please refer to the original specifications for a more comprehensive discussion of security issues.The following example was originally given in RFC 2617 and is expanded here to show the full text expected for each request and response. Note that only the "auth" (authentication) quality of protection code is covered – at the time of writing only the Opera and Konqueror web browsers are known to support "auth-int" (authentication with integrity protection). Although the specification mentions HTTP version 1.1 the scheme can be successfully added to a version 1.0 server, as shown here.
This typical transaction consists of the following steps.
- The client asks for a page that requires authentication but does not provide a user name and password. Typically this is because the user simply entered the address or followed a link to the page.
- The server responds with the 401 response code, providing the authentication realm and a randomly-generated, single-use value called anonce.
- At this point, the client will present the authentication realm (typically a description of the computer or system being accessed) to the user and prompt for a user name and password. The user may decide to cancel at this point.
- Once a user name and password have been supplied, the client re-sends the same request but adds an authentication header that includes the response code.
- In this example, the server accepts the authentication and the page is returned. If the user name is invalid and/or the password is incorrect, the server might return the "401" response code and the client would prompt the user again.
Note: A client may already have the required user name and password without needing to prompt the user, e.g. if they have previously been stored by a web browser.
Client request (no authentication):
GET /dir/index.html HTTP/1.0 Host: localhost
Server response:
HTTP/1.0 401 Unauthorized Server: HTTPd/0.9 Date: Sun, 10 Apr 2005 20:26:47 GMT WWW-Authenticate: Digest realm="[email protected]", qop="auth,auth-int", nonce="dcd98b7102dd2f0e8b11d0f600bfb0c093", opaque="5ccc069c403ebaf9f0171e9517f40e41" Content-Type: text/html Content-Length: 311 <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN" "http://www.w3.org/TR/1999/REC-html401-19991224/loose.dtd"> <HTML> <HEAD> <TITLE>Error</TITLE> <META HTTP-EQUIV="Content-Type" CONTENT="text/html; charset=ISO-8859-1"> </HEAD> <BODY><H1>401 Unauthorized.</H1></BODY> </HTML>
Client request (user name "Mufasa", password "Circle Of Life"):
GET /dir/index.html HTTP/1.0
Host: localhost
Authorization: Digest username="Mufasa",
realm="[email protected]",
nonce="dcd98b7102dd2f0e8b11d0f600bfb0c093",
uri="/dir/index.html",
qop=auth,
nc=00000001,
cnonce="0a4f113b",
response="6629fae49393a05397450978507c4ef1",
opaque="5ccc069c403ebaf9f0171e9517f40e41"
(followed by a blank line, as before).
Server response:
HTTP/1.0 200 OK Server: HTTPd/0.9 Date: Sun, 10 Apr 2005 20:27:03 GMT Content-Type: text/html Content-Length: 7984
(followed by a blank line and HTML text of the restricted page).
The "response" value is calculated in three steps, as follows. Where values are combined, they are delimited by colon symbols.
- The MD5 hash of the combined user name, authentication realm and password is calculated. The result is referred to as HA1.
- The MD5 hash of the combined method and digest URI is calculated, e.g. of "GET" and "/dir/index.html". The result is referred to as HA2.
- The MD5 hash of the combined HA1 result, server nonce (nonce), request counter (nc), client nonce (cnonce), quality of protection code (qop) and HA2 result is calculated. The result is the "response" value provided by the client.
Since the server has the same information as the client, the response can be checked by performing the same calculation. In the example given above the result is formed as follows – where MD5() represents a function used to calculate an MD5 hash, backslashes represent a continuation and the quotes shown are not used in the calculation.
Completing the example given in RFC 2617 gives the following results for each step.
HA1 = MD5( "Mufasa:[email protected]:Circle Of Life" ) = 939e7578ed9e3c518a452acee763bce9 HA2 = MD5( "GET:/dir/index.html" ) = 39aff3a2bab6126f332b942af96d3366 Response = MD5( "939e7578ed9e3c518a452acee763bce9:\ dcd98b7102dd2f0e8b11d0f600bfb0c093:\ 00000001:0a4f113b:auth:\ 39aff3a2bab6126f332b942af96d3366" ) = 6629fae49393a05397450978507c4ef1
At this point the client may make another request, reusing the server nonce value (the server only issues a new nonce for each "401" response) but providing a new client nonce (cnonce). For subsequent requests, the hexadecimal request counter (nc) must be greater than the last value it used – otherwise an attacker could simply "replay" an old request with the same credentials. It is up to the server to ensure that the counter increases for each of the nonce values that it has issued, rejecting any bad requests appropriately. Obviously changing the method, URI and/or counter value will result in a different response value.
The server should remember nonce values that it has recently generated. It may also remember when each nonce value was issued, expiring them after a certain amount of time. If an expired value is used, the server should respond with the "401" status code and add stale=TRUE to the authentication header – indicating that the client should re-send with the new nonce provided, without prompting the user for another user name and password.
The server does not need to keep any expired nonce values – it can simply assume that any unrecognised values have expired. It is also possible for the server to only allow each nonce value to be returned once, although this forces the client to repeat every request. Note that expiring a server nonce immediately will not work, as the client would never get a chance to use it.
[edit]SIP Digest Authentication
SIP uses basically the same digest authentication algorithm. It is specified by RFC 3261.
[edit]Browser Implementation
Browsers that have fully implemented the spec:
[edit]References
[edit]See also
[edit]External links
關鍵看OVERVIEW開始的那一部份. 涉及的2617,2069還有SIP的RFC能看也看, 下面看看怎麼來解決這個401的問題. 從上文及下面的例子可以得出一個結論, 要成功驗證,需要通過MD5的演算法來加密併發送驗證資訊給SERVER. 來看看上面401的請求要如何加密: 從這裡提取所需要的驗證資訊: WWW-Authenticate: Digest qop="auth",stale=false,realm="ocp.gz.com",opaque="242a40eaaadcf7d4f96838f5b047219f",nonce="MTI2OTU2Nzk5NjU0NDY2NTdlM2ZiYjkyNjcyYzIyNGI1OWMwNmVkNDA0MmRj" username:anson password: 12345 qop: auth realm: ocp.gz.com nonce: MTI2OTU2Nzk5NjU0NDY2NTdlM2ZiYjkyNjcyYzIyNGI1OWMwNmVkNDA0MmRj 另外的一些資訊: method: REGISTER uri: sip:ocp.gz.com nc: 00000001 cnonce: 42BA2693 附:MD5加密演算法 public class md5 { public static String md5s(String plainText) { String md5String = ""; try { MessageDigest md = MessageDigest.getInstance("MD5"); md.update(plainText.getBytes()); byte b[] = md.digest(); int i; StringBuffer buf = new StringBuffer(""); for (int offset = 0; offset < b.length; offset++) { i = b[offset]; if (i < 0) i += 256; if (i < 16) buf.append("0"); buf.append(Integer.toHexString(i)); } md5String = buf.toString(); } catch (NoSuchAlgorithmException e) { // TODO Auto-generated catch block e.printStackTrace(); } return md5String; } 這是從網上搜來的資料: 接著用MD5加密 String ha1 = md5s(username + ":" + realm + ":" + password); String ha2 = md5s(method + ":" + uri); 最後的加密: String response = md5s(ha1 + ":" + nonce + ":" + nc + ":" + cNonce + ":" + qop + ":"+ ha2); 取得的response在下面會有用到: 在這裡加密驗證完成, 重構請求如下: REGISTER sip:ocp.gz.com SIP/2.0 Call-ID: [email protected] From: "anson" <sip:[email protected]:5060>;tag=textclientv1.0 To: <sip:[email protected]> Via: SIP/2.0/TCP ocp.gz.com:5060;branch=branch1 Max-Forwards: 70 Contact: "anson" <sip:[email protected]:5060> Authorization: Digest response="b7431ac8d32d35a5dcfcc9f94a3bf714",cnonce="42BA2693",username="anson",nc=00000001,qop=auth,nonce="MTI2OTU2ODg3ODc5NDk2MDkwYjg4YmI4YjMwYzk0MDNmYzg4NzY2ZDg5MDUy",realm="ocp.gz.com",opaque="f14f98a15aa2f710a444d1bc4a23c5dc",uri="sip:ocp.gz.com" CSeq: 2 REGISTER Content-Length: 0 最後,伺服器的響應: SIP/2.0 200 OK Via: SIP/2.0/TCP ocp.gz.com:5060;branch=branch1;received=192.168.2.1 To: <sip:[email protected]>;tag=-1knbda37mzjvk1690651699 From: "anson" <sip:[email protected]:5060>;tag=textclientv1.0 Call-ID: [email protected] CSeq: 2 REGISTER Server: Oracle-OCMS/10.1.3.4.0 Supported: path,pref Contact: "anson" <sip:[email protected]:5060>;methods="INVITE,BYE,CANCEL,ACK,OPTIONS";expires=3600 P-Associated-URI: <sip:[email protected]> Content-Length: 0 自此,一個REGISTER的請求才算完成.相關推薦
收到伺服器401響應的處理(HTTP或SIP)
Digest access authentication HTTP Digest access authentication is one of the agreed methods a web server can use to negotiate credentials with a web user (
(二)servlet處理Http響應
web nbsp 購物車 res 請求 head 自動 地址 發生 重定向:web服務器收到客戶端的請求後,通知客戶端發送一個新的請求到另一個房web服務器。 resp.sendRedirect("URL"); 特點:1)客戶端發送兩次請求 2)瀏
Http響應處理
head 組成 mime 客戶端 tco encoding ets 字節 out 軟件152 羅傑 1. Http響應內容: a) 響應狀態:狀態碼和狀態信息組成 i. 狀態碼: 1. 1XX:用於指定客戶端應響應的某些動作 2. 2XX:用於
Go語言中處理 HTTP 伺服器
文章目錄 1 概述 2 http.Server 型別 3 http.DefaultServeMux 預設路由物件 4 處理器 1 概述 包 net/http 提供了HTTP伺服器端和客戶端的實現。本文說
REST(三)處理HTTP狀態碼、異常和響應頭
REST(三)處理HTTP狀態碼、異常和響應頭 之前的內容只是討論了正確的處理結果,而沒有討論當沒有找到資源時的處理或者發生異常時的處理。當發生資源找不到或者處理邏輯發生異常時,需要考慮的時返回給客戶端HTTP抓鬼你太嗎和錯誤訊息的問題。為了簡化這些開發,Spring提供了實體封裝類
概述和HTTP請求 和 響應處理
1、概述 爬蟲,應該稱為網路爬蟲,也叫網頁蜘蛛人,網路螞蟻等 搜尋引擎,就是網路爬蟲的應用者 2、爬蟲分類 通用爬蟲: 常見就是搜尋引擎,無差別的收集資料,儲存,提交關鍵字,構建索引庫,給使用者提供搜尋介面 爬取一般流程: 1、初始一批URL,將這些URL
Laravel構建API伺服器之響應資料處理
這篇文章主要講述在使用Laravel構建API服務時,如何利用Laravel生態社群中的第三方元件對響應的資料進行處理。 (不做相關詳細使用方法的介紹) 相關元件: 1. dingo/api:一個為了更加快速、方便的構建Restful API而生的Laravel、L
自己的web伺服器專案-request請求和response響應處理(一)
我們經常使用別人的伺服器進行構建網站,現在我們就自己來寫一個自己的服務來使用。 一、request請求獲取 1、瞭解request請求 在寫伺服器之前,我們需要知道客戶端傳送給我們哪些資訊?以及要求我們返回哪些資訊?經過測試我們能夠知道使用者客戶端傳送的資訊有以下
Timeout 時間已到。在操作完成之前超時時間已過或伺服器未響應。 (.Net SqlClient Data Provider)
原文地址 在做一個小東西的時候出現了這個問題,就是使用VS除錯幾次專案後,使用SQL Server Management Studio管理資料庫時,使用SA登入就會出現這個錯誤,當然,如果專案中的資料庫連線字串中使用的sa驗證,那麼專案也會連不到資料庫
Servlet-處理HTTP請求與響應
HttpServletRequest HttpServletRequest 物件代表客戶端的請求,客戶端的所有訊息都封裝在這個物件中,通過這個方法可以獲取請求資料 作用: 讀取和寫入HTTP請求資料 取得和設定Cookies 取得路徑資訊 標識HTTP資
解決ASP.NET Web Applicatio超時時間已到.在操作完成之前超時時間已過或伺服器未響應
“超時時間已到。在操作完成之前超時時間已過或伺服器未響應”初步分析原因為對MSSQL操作時連線超時,知道這事,以前沒留意,大概是在配置檔案中設定連線時限,在網上找了下解決方法,大多說在資料庫連線字串裡解決 SqlConnection con = new SqlConnec
C# SQL語句執行時間過長在操作完成之前超時時間已過或伺服器未響應問題的解決
SqlCommand sold_cmd = new SqlCommand(sql_sold,conn); sold_cmd.CommandTimeout = 300; SqlCommand detail_c
JavaWeb(三) ----Servlet處理HTTP響應,請求
Servlet處理HTTP響應 設定響應狀態行 狀態行:HTTP協議,狀態碼,狀態描述。 HTTP狀態碼: 1. 100-199 :表示資訊性程式碼,標示客戶端應該採取其他動作,請求正在進行。 2. 200-299 :表示客戶請求成功。 3. 3
servlet處理HTTP響應——設定訊息響應體
我們最先要討論的功能是:如何將資訊返還給客戶端? HttpServletResponse物件就是負責此功能的。 但是,HttpServletResponse物件本甚只產生一個空的HTTP響應。 傳
Web伺服器處理HTTP壓縮之gzip、deflate壓縮
一、什麼是gzip gzip是一種資料格式,預設且目前僅使用deflate演算法壓縮data部分; Gzip是一種流行的檔案壓縮演算法,現在的應用十分廣泛,尤其是在Linux平臺。當應用Gzip壓縮到一個純文字檔案時,效果是非常明顯的,
Servlet生命週期和處理Http請求與響應
servlet的生命週期: 1.容器開啟並載入servlet; 2.呼叫init()方法對servlet進行初始化; 3.當請求到來呼叫service()方法處理請求,傳送響應; 4.呼叫destory()方法銷燬servlet; servlet處理Http響應
使用SQL語句備份資料庫時,出現如下錯誤:“超時時間已到。在操作完成之前超時時間已過或伺服器未響應。”
解決方案 如果用SqlCommand物件執行SQL語句,那麼只需要將sqlCommand的超時時間設定為0即可。(0表示沒有限制) SqlCommand cmd = new SqlCo
在IIS伺服器上未能載入檔案或程式集“System.Web.Http, Version=4.0.0.0, Culture=neutral
在WindowsServers2012+IIS6.0上釋出任務時出現了一下三個錯誤: 未能載入檔案或程式集“System.Web.Http, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad
VC連線HTTP伺服器 & MFC 處理 HTTP 請求的基本方法
用 MFC 發起 HTTP Post 請求,主要流程和 MFC HTTP Get 程式碼一樣,以下是示例程式碼: //通過 http POST 協議來發送命令給伺服器 CInternetSession session; session.SetOption(INTERNET_OPTION_CONNECT_TI
Sql Server超時時間已到。在操作完成之前超時時間已過或伺服器未響應[總結]
[Sql Server]超時時間已到。在操作完成之前超時時間已過或伺服器未響應。 針對這個問題可以從以下幾個房方面考慮:(若您有高見,請留言,謝謝) 一:執行命令超時; SqlCom
