【jarvisoj刷題之旅】pwn題目Tell Me Something的writeup
阿新 • • 發佈:2018-10-31
題目資訊:
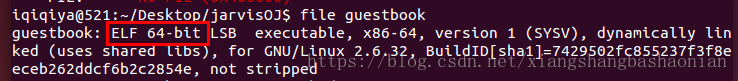
file一下 發現是64位的ELF
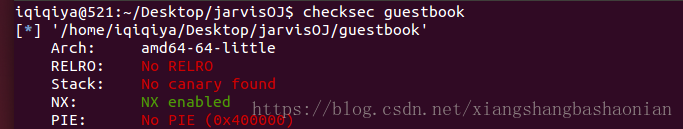
checksec檢查下安全性
objdump -t 檔名 可以檢視符號表
[email protected]:~/Desktop/jarvisOJ$ objdump -t guestbook guestbook: file format elf64-x86-64 SYMBOL TABLE: 0000000000400200 l d .interp 0000000000000000 .interp 000000000040021c l d .note.ABI-tag 0000000000000000 .note.ABI-tag 000000000040023c l d .note.gnu.build-id 0000000000000000 .note.gnu.build-id 0000000000400260 l d .gnu.hash 0000000000000000 .gnu.hash 0000000000400280 l d .dynsym 0000000000000000 .dynsym 0000000000400328 l d .dynstr 0000000000000000 .dynstr 0000000000400378 l d .gnu.version 0000000000000000 .gnu.version 0000000000400388 l d .gnu.version_r 0000000000000000 .gnu.version_r 00000000004003a8 l d .rela.dyn 0000000000000000 .rela.dyn 00000000004003c0 l d .rela.plt 0000000000000000 .rela.plt 0000000000400450 l d .init 0000000000000000 .init 0000000000400470 l d .plt 0000000000000000 .plt 00000000004004e0 l d .text 0000000000000000 .text 0000000000400704 l d .fini 0000000000000000 .fini 0000000000400710 l d .rodata 0000000000000000 .rodata 0000000000400768 l d .eh_frame_hdr 0000000000000000 .eh_frame_hdr 00000000004007b0 l d .eh_frame 0000000000000000 .eh_frame 00000000006008d8 l d .init_array 0000000000000000 .init_array 00000000006008e0 l d .fini_array 0000000000000000 .fini_array 00000000006008e8 l d .jcr 0000000000000000 .jcr 00000000006008f0 l d .dynamic 0000000000000000 .dynamic 0000000000600ac0 l d .got 0000000000000000 .got 0000000000600ac8 l d .got.plt 0000000000000000 .got.plt 0000000000600b10 l d .data 0000000000000000 .data 0000000000600b20 l d .bss 0000000000000000 .bss 0000000000000000 l d .comment 0000000000000000 .comment 0000000000000000 l df *ABS* 0000000000000000 crtstuff.c 00000000006008e8 l O .jcr 0000000000000000 __JCR_LIST__ 0000000000400550 l F .text 0000000000000000 deregister_tm_clones 0000000000400590 l F .text 0000000000000000 register_tm_clones 00000000004005d0 l F .text 0000000000000000 __do_global_dtors_aux 0000000000600b20 l O .bss 0000000000000001 completed.6661 00000000006008e0 l O .fini_array 0000000000000000 __do_global_dtors_aux_fini_array_entry 00000000004005f0 l F .text 0000000000000000 frame_dummy 00000000006008d8 l O .init_array 0000000000000000 __frame_dummy_init_array_entry 0000000000000000 l df *ABS* 0000000000000000 pwn100.c 0000000000000000 l df *ABS* 0000000000000000 crtstuff.c 00000000004008d0 l O .eh_frame 0000000000000000 __FRAME_END__ 00000000006008e8 l O .jcr 0000000000000000 __JCR_END__ 0000000000000000 l df *ABS* 0000000000000000 00000000006008e0 l .init_array 0000000000000000 __init_array_end 00000000006008f0 l O .dynamic 0000000000000000 _DYNAMIC 00000000006008d8 l .init_array 0000000000000000 __init_array_start 0000000000600ac8 l O .got.plt 0000000000000000 _GLOBAL_OFFSET_TABLE_ 0000000000400700 g F .text 0000000000000002 __libc_csu_fini 0000000000000000 w *UND* 0000000000000000 _ITM_deregisterTMCloneTable 0000000000600b10 w .data 0000000000000000 data_start 0000000000000000 F *UND* 0000000000000000[email protected]@GLIBC_2.2.5 0000000000600b20 g .data 0000000000000000 _edata 0000000000400704 g F .fini 0000000000000000 _fini 0000000000000000 F *UND* 0000000000000000 [email protected]@GLIBC_2.2.5 0000000000000000 F *UND* 0000000000000000 [email protected]@GLIBC_2.2.5 0000000000000000 F *UND* 0000000000000000 [email protected]@GLIBC_2.2.5 0000000000600b10 g .data 0000000000000000 __data_start 0000000000000000 w *UND* 0000000000000000 __gmon_start__ 0000000000600b18 g O .data 0000000000000000 .hidden __dso_handle 0000000000400710 g O .rodata 0000000000000004 _IO_stdin_used 0000000000400690 g F .text 0000000000000065 __libc_csu_init 0000000000600b28 g .bss 0000000000000000 _end 0000000000400526 g F .text 0000000000000000 _start 0000000000600b20 g .bss 0000000000000000 __bss_start 00000000004004e0 g F .text 0000000000000046 main 0000000000000000 F *UND* 0000000000000000[email protected]@GLIBC_2.2.5 0000000000000000 w *UND* 0000000000000000 _Jv_RegisterClasses 0000000000400670 g F .text 000000000000001e readmessage 0000000000600b20 g O .data 0000000000000000 .hidden __TMC_END__ 0000000000000000 w *UND* 0000000000000000 _ITM_registerTMCloneTable 0000000000400450 g F .init 0000000000000000 _init 0000000000400620 g F .text 000000000000004a good_game
這裡可以看到good_game很可疑
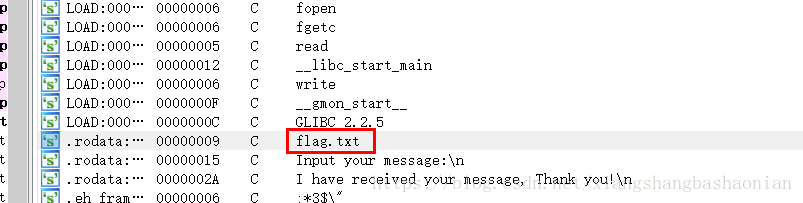
IDA 分析一下也可以看到flag.txt,read,read等
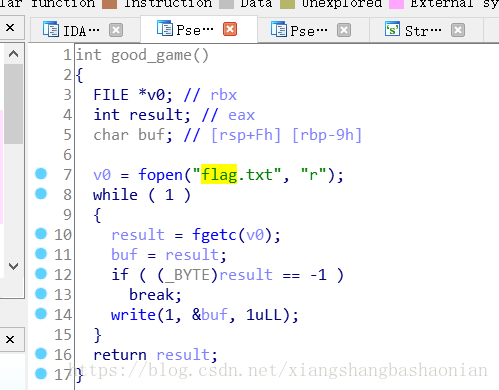
分別雙擊這個Input your message 和flag.txt 的引用 然後F5
那麼我們就可以判斷出good_game()這個函式的作用就是開啟flag.txt並讀取內容輸出
main()是沒有呼叫它的 也就是說程式正常是無法執行good_game()的
但是可以看到main()中有呼叫read(),那麼我們就可以通過向緩衝區中輸入大於 buf 長度的資料 , 這樣多餘的資料就會溢位 , 並覆蓋棧上的一些資料,那麼我們就將main()函式的返回地址改成good_game()的入口地址,這樣就可以在main()執行完之後輸出flag.txt內容了
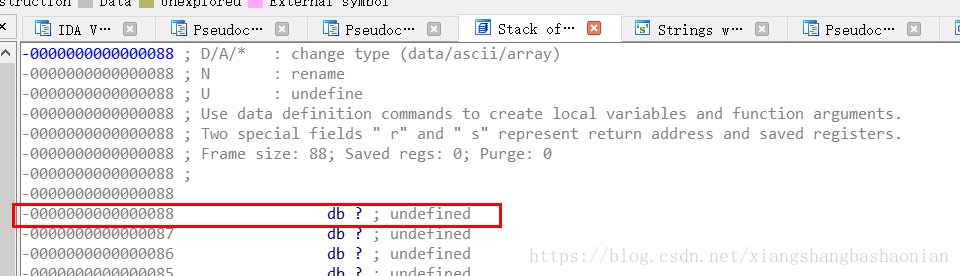
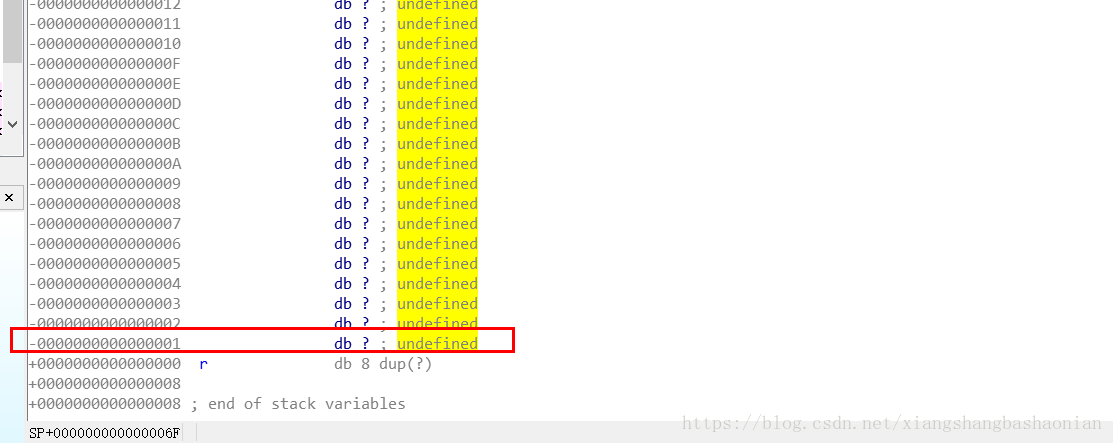
雙擊main()中的v4 就可以檢視main函式的棧幀
可以看到 , 用於緩衝使用者輸入的字元陣列距離 main 的返回地址有 0x88 個位元組
那麼我們需要輸入 0x88 (136) 個位元組的資料 , 再輸入 good_game 的地址 , 這樣程式返回的時候就會跳轉到 good_game 去執行
通過 ida 來檢視 good_game 的地址
需要轉換成小端序的形式 , 可以利用zio這個庫
我直接用pwntools
指令碼如下: